Industrial Cyber Threat Intelligence
Discover the most advanced Cyber Threat Intelligence system ever.
contact us
"Intelligence is a corporate capability to forecast change in time to do something about it. The capability involves foresight and insight, and is intended to identify impending change, which may be positive, representing opportunity, or negative, representing threat."
About Us
Our company is specially engaged in the development of a CTI (Cyber Threat Intelligence) solutions with ICS (Industrial Control System) focus and Industrial Honeynet Systems (IHS). In 2019, our product won the ITBusiness Awards product development grand prize. With our 100 percent proprietary solutions, we strive to provide an effective solution to emerging CTI challenges in both industrial and critical infrastructure environments.
In addition to development, we are passionate about gathering information, so we also place a great emphasis on threat hunting activities.
Our team consists mainly of talented young people, but of course there are also some of us with 15-20 years of experience in either software development or intelligence.
In our products, services and capabilities, we strive for professional efficiency in the field of CTI as widely as possible.

Latest News
Read MoreServices
CTI-as-a-Service
Complex CTI software system with ICS specifics. The essence of CTI is that before the incident occurs, we collect data on possible attackers, methodologies, directions, motivations in the most varied ways. Accordingly, the software system provides dynamic protection, not static protection.
Intel Services
We collect the widest possible data (darknet, clearweb) on the Internet in order to feed our complex CTI system with sufficient Intelligence (Intel) data. This constantly, dynamically expanding Data Lake allows us to search for entities in a targeted way or in forums operating on the Dark Web.
Products
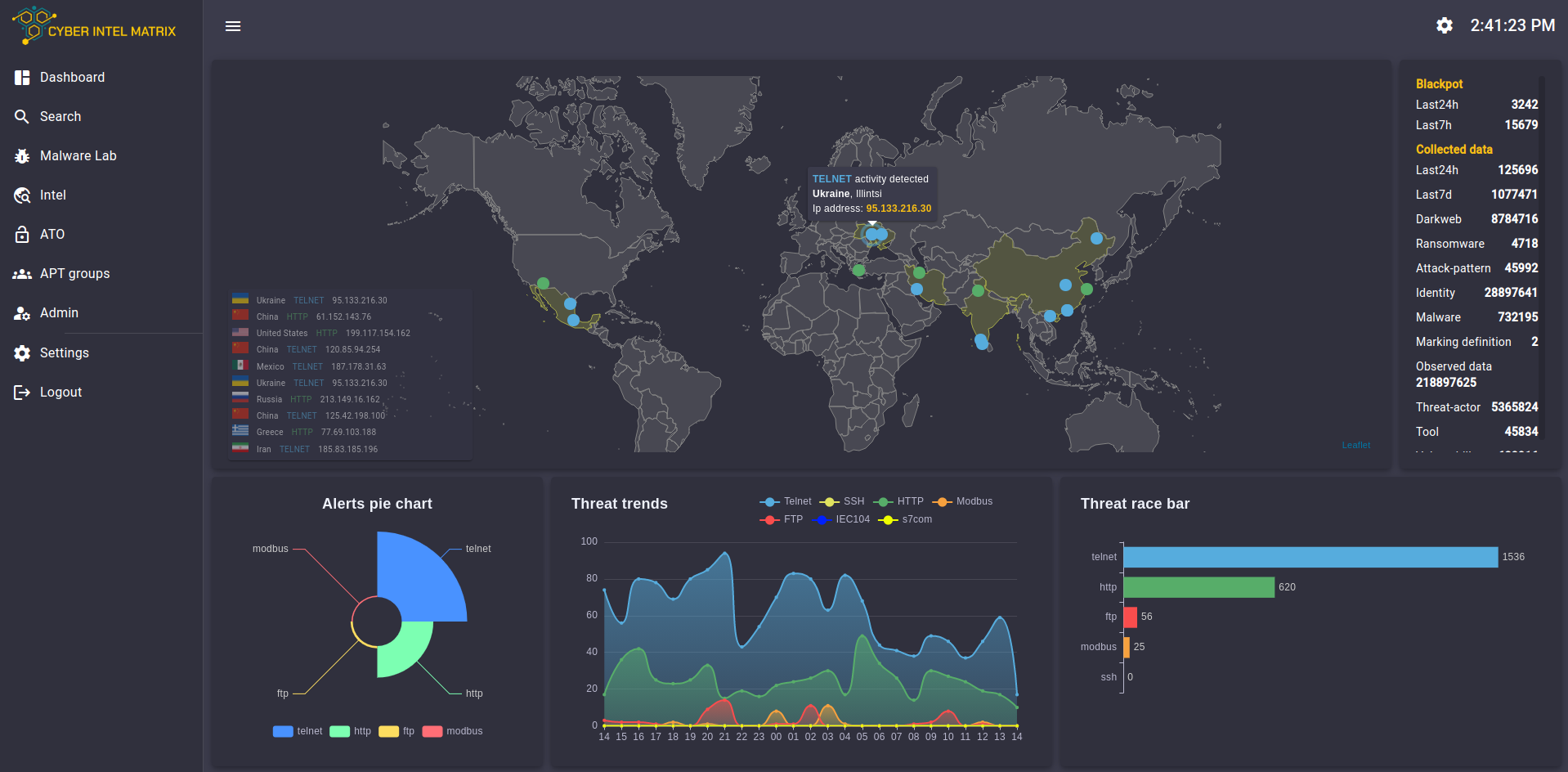
CyberIntelMatrix Platform
The essence of the system and the basis of its success is that it does not focus on static defense capability, but on Threat Hunting activity, i.e. attack prevention, risk-threat identification with automated information collection and classification even before the attack.
Within the system, we operate solutions such as Blackpots, Malwerlab, STIX Graph and cyber threat intelligence.
The system collects information about attacking devices, threatening locations, methods, and information needed to identify an attacker. From this data we can deduce motivations and specific directions of attack.
The system specializes in ICS, i.e. industrial controllers, with worldwide coverage based on a Blackpot system with 150+ custom-developed (proprietary) and installed industrial controllers.
ICS Threat Feed
CIM provides first-hand information about attacks on both general IT infrastructure and the most common ICS protocols through its proprietary honeynet system.
Addition to this, we perform various types of information gathering on a daily basis, both manually and automatically, using a specialized methodology. We create specific databases (data lake), we use AI-driven algorithms in both data collection and data processing analysis. We also carry out SOCMINT activities.
The essence of the service is that we can monitor and search for entities on both the clear web and the dark web, either in static sources or in dynamic daily collected sources.

Law Enforcement
We can make our data collection and development capabilities and experience available to state bodies with special needs and authorization in order to enhance or entirely carry out their effective law enforcement activities.
Partner Program
Our simple, profitable and flexible partner program will help you grow your business by providing solutions that are easy to demo, easy to sell, and easy to manage. Our dedicated channel team is always there for you. You’ll be able to offer unparalleled customer support and satisfaction. And you’ll benefit from our aggressively competitive discounts and deal registration, joint lead generation programs, and first-class training and certification programs.
Our Partners:



Benefits:
- Recurring revenue
- Higher value higher fee
- Strict deal/lead protection
- Marketing materials
- Training and certification programs
- Pre-sales support
Categories:
- System integrators
- Value-Added Resellers
- Managed Security Service Providers
- Solution Providers
Free membership registration